- (+91) 44223 92820
- (+91) 89036 01585
- info@saishanbusiness.in
SAP Process Audit
Based on a solid SAP implementation and support after implementation to clients in and out
of India including major MNCs, over a period of 15 years, founder of this company can
provide very good insight and support under the following fronts in
a highly professional manner. Most of them are multinational clients spread over different
World Geography.
It is an area how an organization uses its SAP system to ensure data integrity, compliance,
and security. It covers both
functional (business processes) and technical (system configuration, access, etc.) aspects
of SAP system.
Functional
In the functional side we identify the business processes relating to Core and Support businesses. Upon identification of processes, we ensure that strong inbuilt internal control system is available in the said processes. Mapping of such control system in the SAP defined Best Business Practices will be checked thoroughly.Technical
In the technical front, we verify the integration points of SAP between different modules. Main integration points are depicited below:- Unless and otherwise the accounts mapped to these points are verified at regular interval based on the business practices and user interaction, it could lead to error in valuation of inventory and the production order. Business decision taken on improper valuation could lead to major consequences.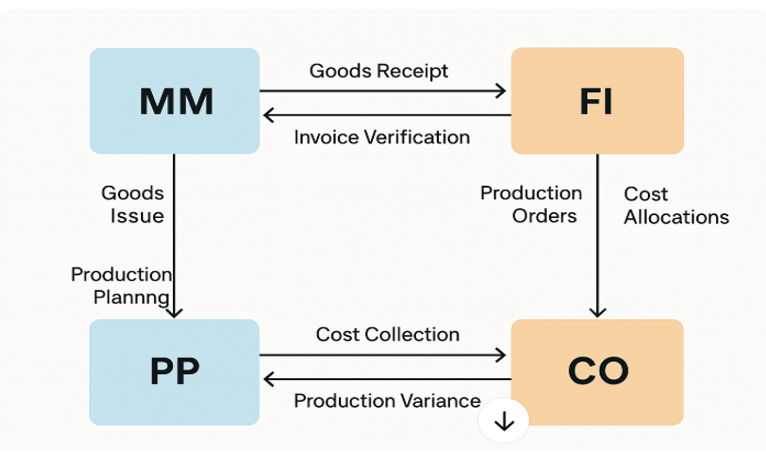
Integration Between SAP MM, PP, CO, and FI
End-to-End Integration at High Level
- MM: Raw materials purchased → Goods Receipt posted → Inventory increased in FI
- PP: Production order created → Raw materials issued (MM) → Costs collected (CO)
- PP: Production confirmed → Labor/machine time posted to CO
- PP: Finished goods received → Inventory value updated in FI
- CO: Order settled → Variances posted to FI GL accounts
- FI: Full financial trail available for audit/reporting
